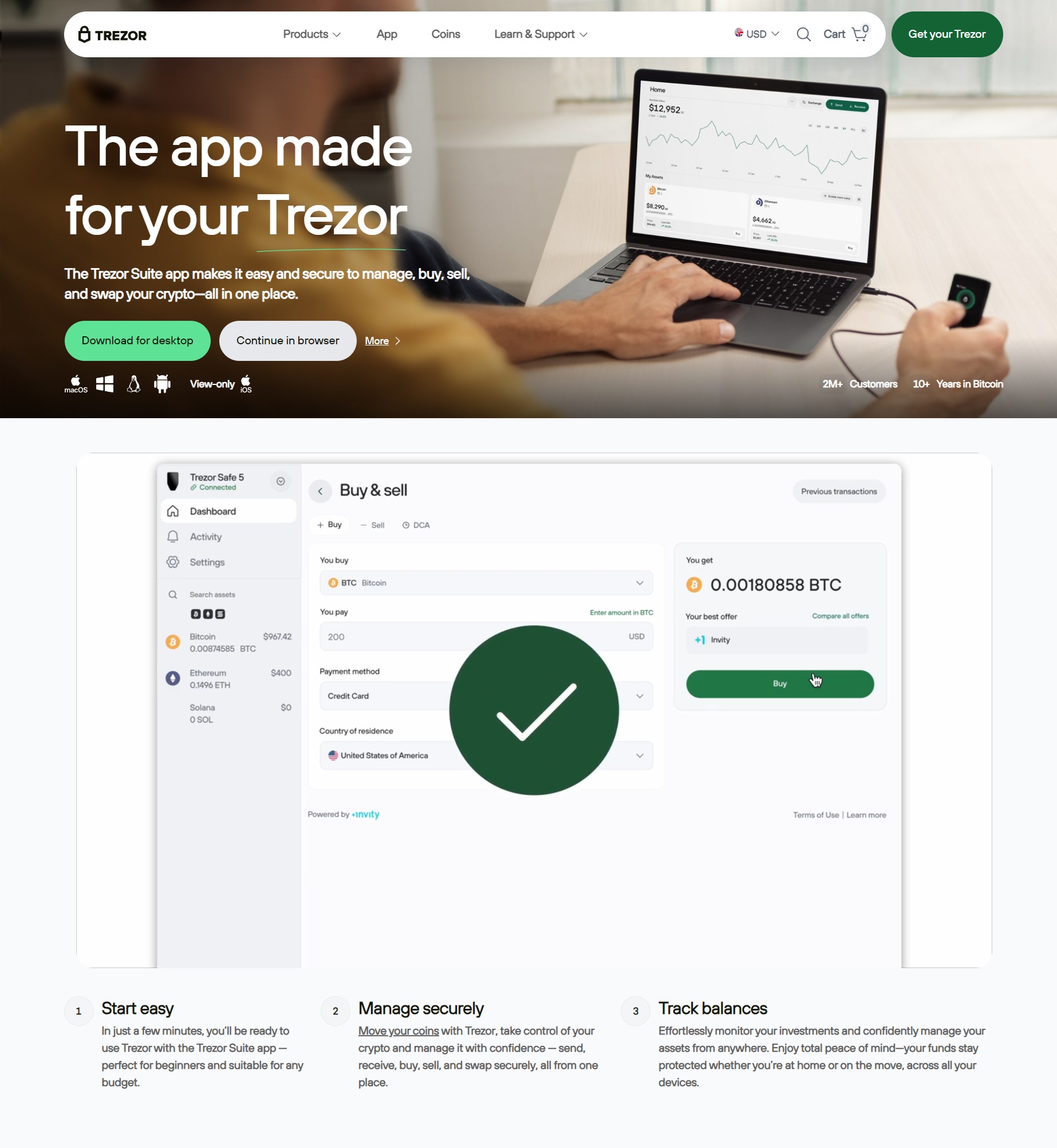
Trezor.io/Start® — Starting Up Your Device | Trezor®
Setting up a hardware wallet is one of the smartest steps any crypto holder can take. In an era of phishing attacks, exchange hacks, and digital threats, protecting your digital wealth is not optional—it’s essential. Trezor®, one of the most trusted hardware wallet brands, offers a secure, beginner-friendly method of safeguarding cryptocurrencies. The official onboarding path—Trezor.io/Start—is designed to guide users through every step of the activation process, ensuring a safe and smooth experience.
This article presents a detailed, presentation-style, 1500-word guide that walks you through everything you need to know about starting your device, understanding the setup, maintaining security, and using Trezor® confidently.
1. Introduction to Trezor® Hardware Wallets
Cryptocurrencies offer financial freedom, but they also introduce security challenges. Storing private keys on a phone or computer exposes your assets to malware or hacking. A hardware wallet like Trezor Model One or Trezor Model T keeps keys offline, isolated from internet-based risks.
Why Trezor®?
It stores private keys on a secure, offline chip.
It requires physical confirmation for every transaction.
It integrates seamlessly with trusted wallets and blockchain applications.
It supports a wide range of cryptocurrencies.
It uses open-source software for transparency.
From beginners to experts, Trezor® provides the protection and control needed in today’s digital world.
2. Before You Begin: Preparing for Setup
Before visiting Trezor.io/Start, make sure you have everything ready. Proper preparation ensures a smooth, error-free onboarding experience.
What You Need
A genuine Trezor® device (Model One or Model T)
A computer or smartphone with a stable internet connection
The official USB cable included with your device
A private, quiet place where you can safely write down your recovery seed
A notebook or paper to store the seed phrase (never digital storage)
Security Checks Before Setup
When unboxing your device, confirm it is authentic and untampered:
The hologram seal should be intact.
The packaging must look original and undisturbed.
The device should not be pre-configured or start with data already inside.
If anything seems suspicious, stop and contact Trezor Support immediately.
3. Visiting Trezor.io/Start — Your Official Setup Portal
When you navigate to Trezor.io/Start, you are directed to the official onboarding platform. This page provides:
The Trezor Suite download
Security warnings
Firmware installation steps
Instructions for device backup
Guides and troubleshooting resources
This portal ensures you are always using official software and authentic files—crucial for avoiding phishing websites.
4. Installing Trezor Suite
Trezor Suite is the control center for your hardware wallet. It is available for Windows, macOS, and Linux.
Why Trezor Suite?
Manage, send & receive crypto
Track portfolio value
Exchange cryptocurrencies
Access security settings
Verify device authenticity
Update firmware
Download only from Trezor.io/Start—never from unknown websites or file-sharing platforms.
Installation Steps
Choose your operating system.
Download the installer.
Run the installation file.
Launch Trezor Suite and connect your device.
Follow the on-screen prompts to begin initialization.
After installation, the app automatically verifies your device and asks if you want to create a new wallet or recover an old one.
5. Firmware Installation & Updates
New devices often require a firmware update. Firmware is the heart of your hardware wallet—it ensures secure operation and supports new features and coins.
How Firmware Installation Works
Once you connect the device, Suite checks firmware status.
If no firmware exists (new device), you are prompted to install it.
If outdated firmware exists, you’re asked to update it.
You must physically confirm firmware installation on your device.
Firmware updates do not affect your stored coins—they remain safe on the blockchain.
Safety Tips
Only install updates through Trezor Suite.
Never trust firmware from unofficial sources.
Keep your device plugged in during the process.
6. Creating Your Wallet: Starting With a Clean Setup
After firmware installation, you’ll create a brand-new wallet.
The Most Important Step: Generating Your Recovery Seed
Your recovery seed—usually 12, 18, or 24 words—is the single backup to your wallet. Whoever has these words can take your crypto. This is why the seed must be:
Written down offline
Stored in a secure location
Never photographed or saved digitally
Never shared with anyone
The device displays each word one at a time to ensure maximum privacy.
Why the Seed Phrase Matters
If your Trezor device is lost, damaged, or stolen, the seed phrase allows you to restore your funds on any new Trezor or compatible wallet. Without it, recovery is impossible.
7. Setting a PIN for Device Access
Your device will prompt you to set a PIN. This adds physical protection—without the PIN, no one can access the wallet.
PIN Tips:
Use a number that is not easy to guess.
Avoid repeating digits or simple patterns.
Never share the PIN with anyone.
If someone tries to brute-force your PIN, the device increases delay times automatically.
This multi-layered design is why Trezor wallets are trusted worldwide.
8. Exploring Trezor Suite Dashboard
Once your wallet is created, you can start exploring. The dashboard has:
Asset overview
Balance and portfolio statistics
Send/receive functions
Market charts
Device configuration settings
Everything is designed with user-friendly navigation while ensuring maximum security.
Key Features
Receive Crypto: Generate official addresses to receive funds safely.
Send Crypto: Approve all transfers physically on your device.
Buy/Exchange Options: Integrations with trusted providers.
Hidden Wallets: Extra layers of privacy using passphrases.
Security Alerts: Notifications for suspicious activity.
9. How Trezor Ensures Security
Trezor uses advanced mechanisms beyond typical crypto wallets.
Core Security Features
Private keys never leave the device
Physical confirmation required for every action
Open-source architecture for transparency
Firmware signing to prevent tampering
Passphrase support for hidden wallets
PIN protection with self-destruct delays
This combination makes Trezor highly resistant to malware and remote attacks.
10. Managing Coins & Tokens
Trezor supports a wide variety of cryptocurrencies, including:
Bitcoin
Ethereum & ERC-20 tokens
Litecoin
Dogecoin
Cardano
Polkadot
And more
Through Trezor Suite, you can add, hide, or customize account views depending on your preferences.
Using Ethereum & Tokens
For Ethereum ecosystems, Trezor integrates with:
MetaMask
WalletConnect apps
DeFi platforms
This allows safe interaction with decentralized applications while keeping private keys offline.
11. Essential Best Practices for Long-Term Security
Even though Trezor provides powerful protection, your habits matter just as much.
Do’s
Store your recovery seed offline in two safe locations.
Keep Trezor Suite updated.
Only use official Trezor cables and software.
Double-check all receiving addresses.
Avoid public Wi-Fi for sensitive operations.
Don’ts
Never upload your recovery seed online.
Never enter the seed into websites or mobile apps.
Never give access to your device to unknown individuals.
Never fall for “support” scams asking for your seed phrase.
12. Troubleshooting Common Issues
Device Not Connecting?
Try a different USB cable.
Update Trezor Suite.
Restart your computer.
Make sure drivers are installed properly.
Forgot PIN?
Reset the device and restore using your recovery seed.
Lost Seed Phrase?
Unfortunately, without the seed phrase, recovery is impossible. This is why proper backup is critical.
13. Why Trezor.io/Start Remains the Safest Onboarding Path
In crypto security, official verification is everything. Using third-party guides or unofficial software can expose you to risks. Trezor.io/Start ensures you are:
Installing legitimate software
Following correct security processes
Avoiding phishing traps
Receiving official firmware
This is why beginners and professionals always rely on the official onboarding link.
14. Final Thoughts
Starting your Trezor® device through Trezor.io/Start is a simple yet powerful step toward uncompromised crypto security. Whether you hold a little or a lot, a hardware wallet is the foundation of digital ownership. With its transparent design, physical protection layers, and secure firmware ecosystem, Trezor® empowers users to control their crypto safely.
From unboxing your device to backing up your seed phrase and exploring Trezor Suite, this guide ensures you begin your journey confidently. As long as you maintain proper personal security habits, Trezor® will safeguard your digital assets for years to come.